Active Online Tools for Work Productivity
Active online tools for work productivity Active online tools for work productivity and document management…
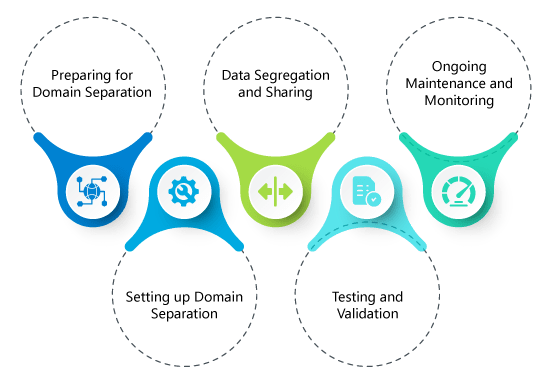
Fortifying Cyber Defenses: The Power of Segregating Domain Registrars, Hosting Providers, Mail Servers, and External Proxy Servers for Enhanced Cybersecurity
Fortifying Cyber Defenses: The Power of Segregating Domain Registrars, Hosting Providers, Mail Servers, and External…
The Alluring Tendency of a Scammer: Unraveling the Dark Charisma
The Alluring Tendency of a Scammer: Unraveling the Dark Charisma Scammers also known as fraudsters…
Taking Action Against Suspicious Emails: A Guide to Reporting Phishing Attempts and Enhancing Online Security
Taking Action Against Suspicious Emails: A Guide to Reporting Phishing Attempts and Enhancing Online Security…
Ethical Hacking: Satisfying My Curiosity While Protecting the Digital World
Ethical Hacking: Satisfying My Curiosity While Protecting the Digital World In a rapidly evolving digital…
The Rise of Fintech Banks: Why They Will Take Over Commercial Banks
The Rise of Fintech Banks: Why They Will Take Over Commercial Banks The financial industry…
Safeguarding Your Digital Assets: Comprehensive Protection Against Cyber Threats
Safeguarding Your Digital Assets: Comprehensive Protection Against Cyber Threats Computer documents are the lifeblood of…
Multitasking: A Vital Competency for Every Technological Professional
Multitasking: A Vital Competency for Every Technological Professional In the fast-paced world of technology, the…
Cryptographic Algorithms: Guardians of Digital Communication
introduction In today's digital age, where communication occurs rapidly and across vast distances, securing sensitive…
Enhancing Work Productivity with Microsoft Copilot
introduction In an ever-evolving digital landscape, the demand for increased work productivity is relentless. To…