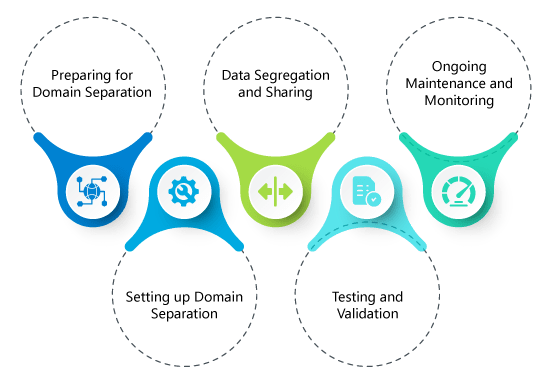
Fortifying Cyber Defenses: The Power of Segregating Domain Registrars, Hosting Providers, Mail Servers, and External Proxy Servers for Enhanced Cybersecurity
Fortifying Cyber Defenses: The Power of Segregating Domain Registrars, Hosting Providers, Mail Servers, and External…