Empowering Digital Libraries with Cloud-Based Services
Empowering Digital Libraries with Cloud-Based Services In today's digital age, the concept of a traditional…
Navigating the Digital Realm: When IT Security Isn’t for Everyone
When IT Security Isn't for Everyone In our increasingly digital world, information technology (IT) tools…
Simple Cybercrime Savvy Tips For Everyone
Simple Cybercrime Savvy Tips For Everyone Cybercrime is a criminal activity that takes place on…
The most significant annual occasion hosted by Apple” – A brief glimpse into what awaits on September 12th.
The most significant annual occasion hosted by Apple Apple's fall event is typically held in…
AFA’s Realistic Nearness: Bridging the Gap Between Reality and Virtuality
AFA's Realistic Nearness: Bridging the Gap Between Reality and Virtuality In our fast-paced, digitally-driven world,…
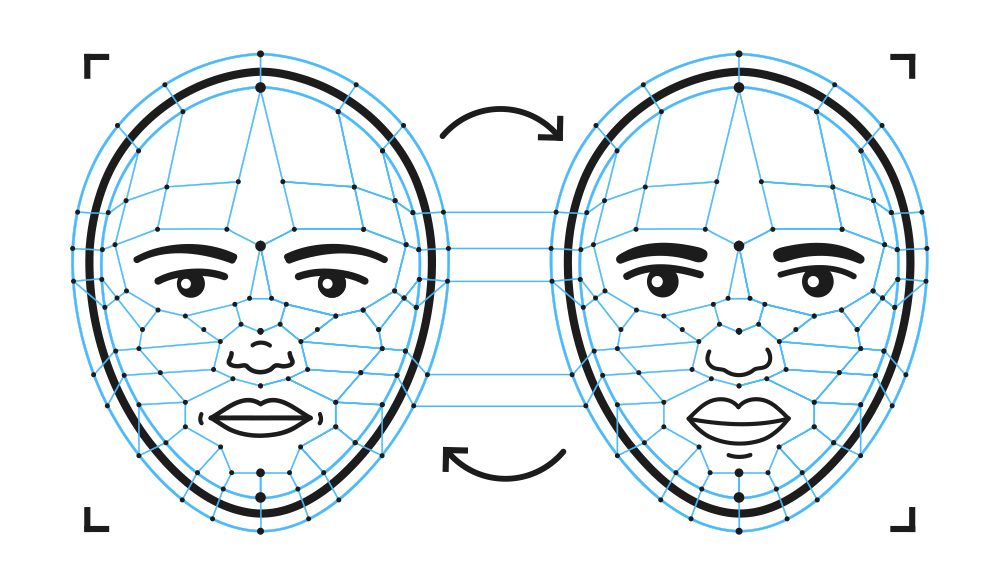
Solution to Deepfake (Deepfake Technology)
SOLUTION TO DEEPFAKE (DEEPFAKE TECHNOLOGY) Deepfake technology has indeed become increasingly sophisticated and accessible, raising…
Understanding Email Attacks: The Anatomy of Email Attacks (a Sneaky Cyber Threat)
INTRODUCTION In the contemporary era of digital technology, electronic mail has evolved into a fundamental…
Unmasking the Shadows: A Deep Dive into the Dark Art of Email Attacks
INTRODUCTION In today's interconnected digital realm, email has become an indispensable part of our personal…
Don’t Just Follow IT Big Names – Embrace the Power of the Unsung Heroes
INTRODUCTION In the constantly changing landscape of technology, it's tempting to be captivated by the…
Exposing the Dark Secrets of Deepfake Technology: Unmasking Scammer Tactics
INTRODUCTION In an era of rapid technological advancement, deepfake technology has emerged as a powerful…