Fortifying Cyber Defenses: The Power of Segregating Domain Registrars, Hosting Providers, Mail Servers, and External Proxy Servers for Enhanced Cybersecurity
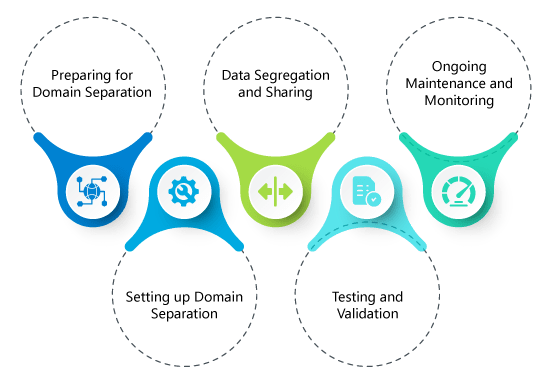
Fortifying Cyber Defenses: The Power of Segregating Domain Registrars, Hosting Providers, Mail Servers, and External Proxy Servers for Enhanced Cybersecurity
In the ever-evolving landscape of cyber threats, safeguarding digital assets has become paramount for businesses and individuals alike. One proactive approach gaining traction is the strategic segregation of domain registrars, hosting providers, mail servers, and the utilization of external proxy servers. This article explores how adopting such practices can significantly mitigate the impact of cyber attacks, adding layers of security and resilience to make it more challenging for attackers to compromise an entire system simultaneously.
Reducing the Attack Surface:
Segregating domain registrars, hosting providers, and mail servers helps in reducing the overall attack surface. When different components of a system are compartmentalized, a successful breach in one area does not automatically grant access to the entire infrastructure. This approach limits the potential impact of an attack and prevents adversaries from gaining a foothold across various aspects of the system.
Diversifying Defense Measures:
By employing a diverse range of service providers, organizations can implement varied security measures tailored to each specific component. This diversity makes it more difficult for attackers to exploit vulnerabilities consistently across different platforms. A weakness in one provider’s security measures may not translate into a vulnerability in another, creating a multi-layered defense strategy.
Enhanced Resilience:
Cyber attackers often target vulnerabilities in a systematic manner, exploiting weaknesses to compromise an entire system. Segregating domain registrars, hosting providers, and mail servers enhances resilience by preventing a single point of failure. Even if one component faces a breach, the remaining segregated elements remain secure, limiting the potential damage and facilitating faster recovery.
External Proxy Servers:
The integration of external proxy servers adds an additional layer of protection by acting as intermediaries between users and the internet. These servers can filter and block malicious traffic before it reaches the organization’s internal network. By obscuring the actual IP address of internal servers, external proxy servers also contribute to a higher level of anonymity, making it harder for attackers to pinpoint and exploit specific vulnerabilities.
Challenges and Considerations:
While the benefits of segregating domain registrars, hosting providers, mail servers, and using external proxy servers are evident, there are challenges to consider. Managing multiple service providers can be complex and requires careful coordination. Additionally, regular monitoring and updates are crucial to ensure that each component remains secure against emerging threats.
Conclusion:
In conclusion, fortifying cybersecurity through the strategic segregation of domain registrars, hosting providers, mail servers, and the use of external proxy servers is a proactive and effective approach. This practice not only reduces the attack surface but also diversifies defense measures, enhances resilience, and creates a formidable barrier against cyber threats. As organizations continue to face increasingly sophisticated attacks, adopting these measures becomes imperative for staying one step ahead in the ongoing battle for digital security.


















4 comments